Recently, some researchers US cybersecurity firm Symantec announced that they found a “highly sophisticated” Chinese hacking tool. It turns out the latter has been used in the past decade but no one could catch it. Symantec call it Daxin and published its research earlier today.
Also Read: Pavel Durov: Apple And Google Are Guilty Of Hacking Smartphones
As a US government official said, they have got it from Symantec recently and shared the information with their foreign partners.
“It’s something we haven’t seen before,” said Clayton Romans, associate director with the US Cybersecurity Infrastructure Security Agency (CISA). “This is the exact type of information we’re hoping to receive.”
Joint Cyber Defence Collaborative Works Effectively
With this statement, Symantec also confirmed its cooperation with the government. We are talking about a public-private cybersecurity information-sharing partnership, JCDC. The latter, which stands for Joint Cyber Defence Collaborative, is a collective of government defense agencies. That’s not difficult to guess that it includes the FBI and National Security Agency as well as 22 US technology companies. Within the cooperation, they share information concerning active cyberattacks.
As expected, the Chinese embassy in Washington did not respond to scmp’s request for comment.
“The capabilities of this malware are remarkable and would be extremely difficult to detect without this public research,” said Neil Jenkins, chief analytics officer at the Cyber Threat Alliance, a non-profit group that brings together cybersecurity experts to share data.
Broadcom’s Symantec team has published a report today on the Daxin backdoor, which they have described as “the most advanced piece of malware Symantec researchers have seen from China-linked actors”
👀👀👀👀👀https://t.co/pHUOXUt8xb pic.twitter.com/iPZLbADsLL
— Catalin Cimpanu (@campuscodi) February 28, 2022
Is This Hacking Tool From China?
Well, many people might think why this hacking tool should come our way from China. In this regard, as Symantec explains, components of Daxin were combined with another Chinese-linked computer hacker infrastructure. So there is every reason to think that this hacking tool comes from China as well.
“The most recent known attacks involving Daxin occurred in November 2021,” the research report reads. But the scale of the intrusions is too large. Also, this tool had an advanced nature and it’s not an easy deal to discover it.
“Daxin’s capabilities suggest the attackers invested significant effort into developing communication techniques that can blend in unseen with normal network traffic.”
According to the report, Daxin’s victims were high-level, non-Western government agencies in Asia and Africa. For instance, it was tracking Ministries of Justice.
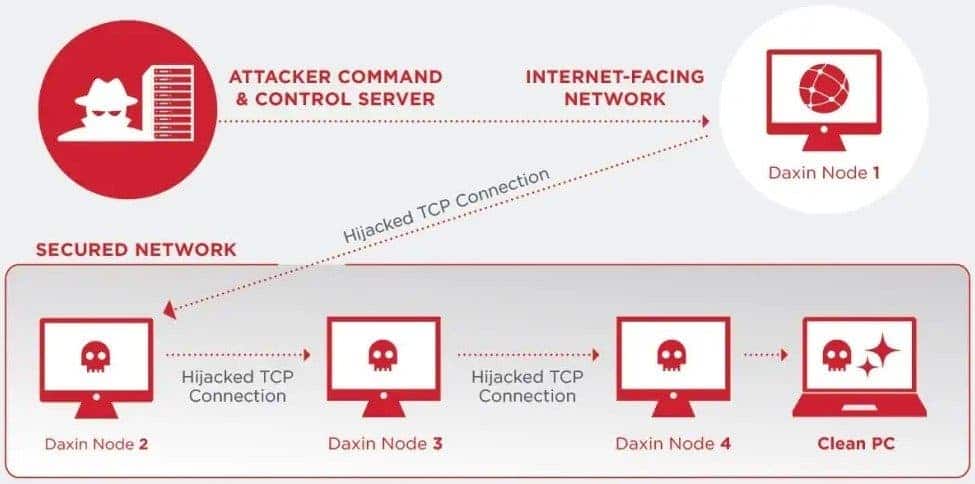
“Daxin can be controlled from anywhere in the world once a computer is actually infected,” said Thakur. “That’s what raises the bar from malware that we see coming out of groups operating from China.”
This tool affected many US organizations. But once discovered, the US government informed about it its partners around the globe.
“Clearly the actors have been successful in not only conducting campaigns but being able to keep their creation under wraps for well over a decade,” Thakur said.







